OneLogin SSO
Follow the sections in this guide to set up OneLogin SSO.
Security requirements for your production environment:
- DELETE the admin default account shipped by OM in case you had Basic Authentication enabled before configuring the authentication with OneLogin SSO.
- UPDATE the Private / Public keys used for the JWT Tokens. The keys we provide by default are aimed only for quickstart and testing purposes. They should NEVER be used in a production installation.
Create Server Credentials
Step 1: Configure a new Application
- Login to OneLogin as an administrator and click on Applications
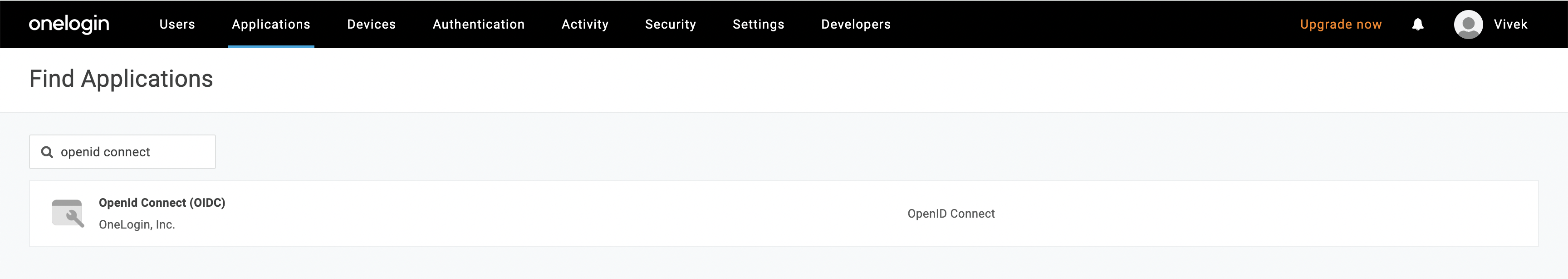
- Click on the
Add Appbutton and search foropenid connect - Select the
OpenId Connect (OIDC)app
- Change the Display Name of the app to
Open Metadataand clickSave

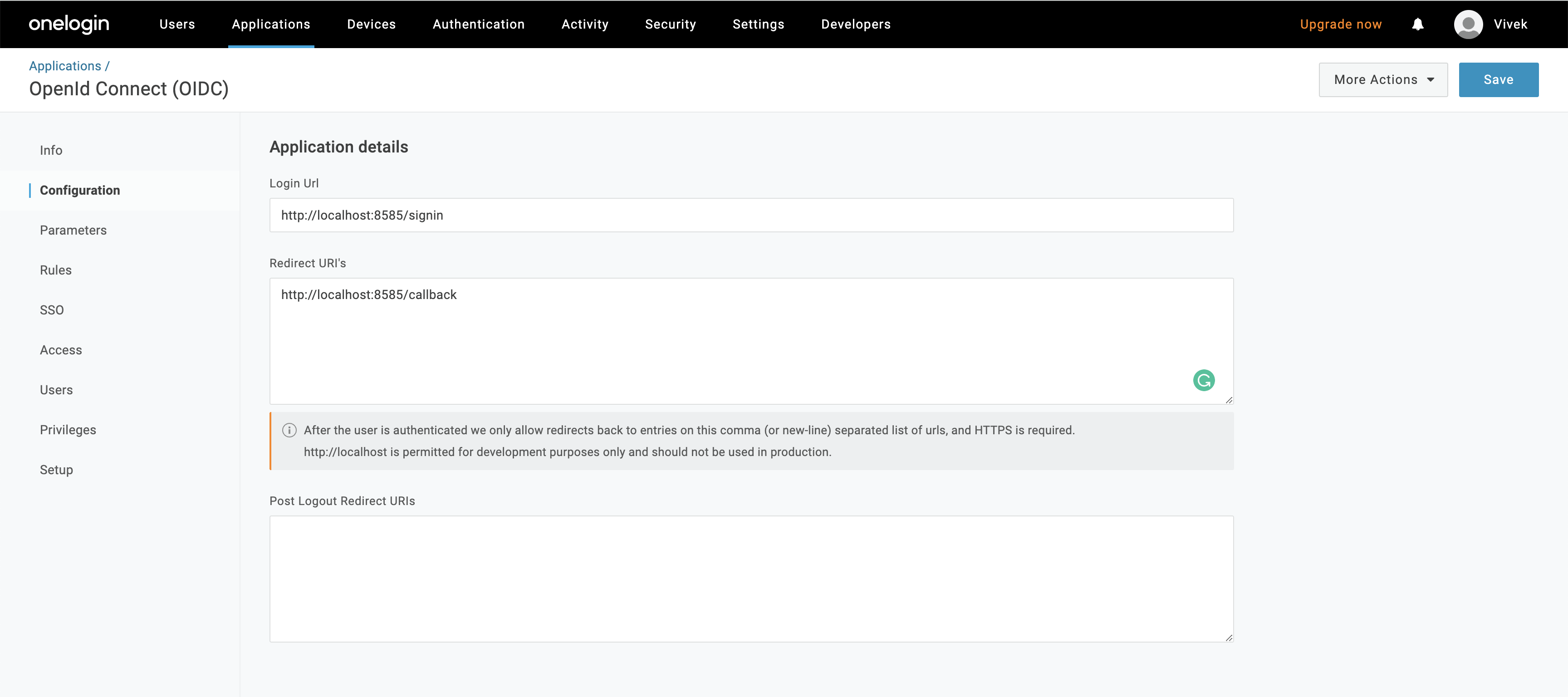
- Configure the login Url (
http(s)://<domain>/signin) and redirect URI (http(s)://<domain>/callback) as shown below
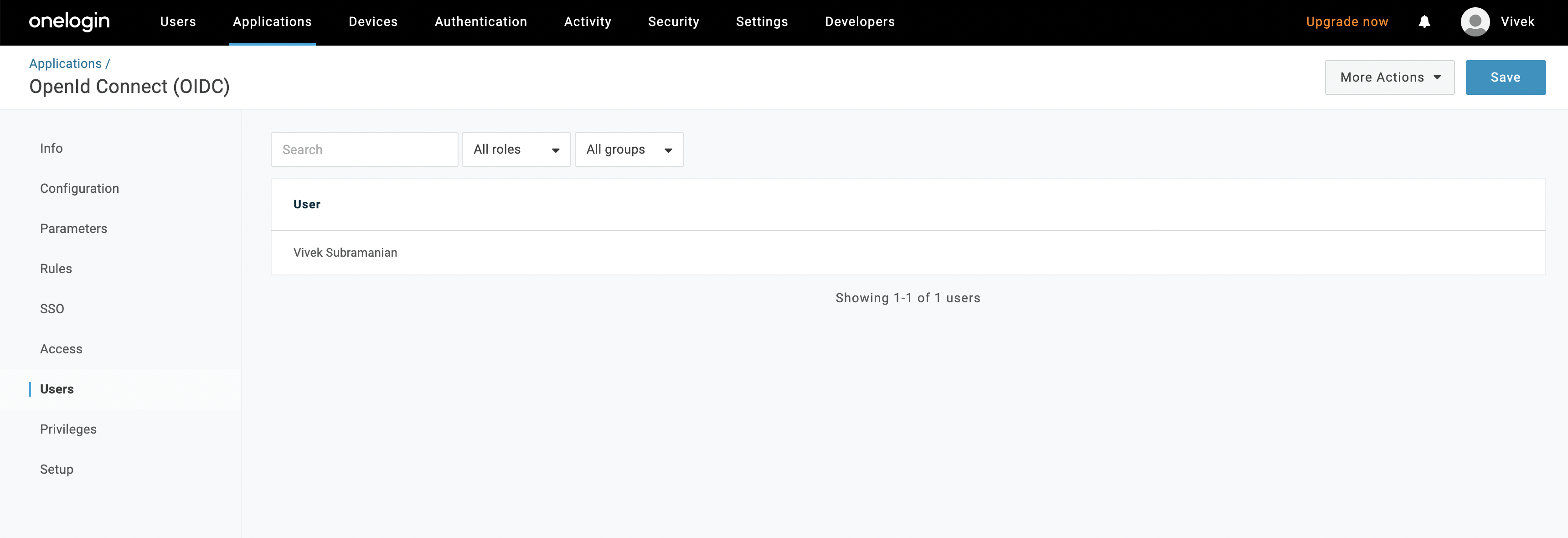
- Configure the users in the organization that can access OpenMetadata app by clicking on the
Users
- Click on "SSO" and select
None (PKCE)for Token Endpoint.
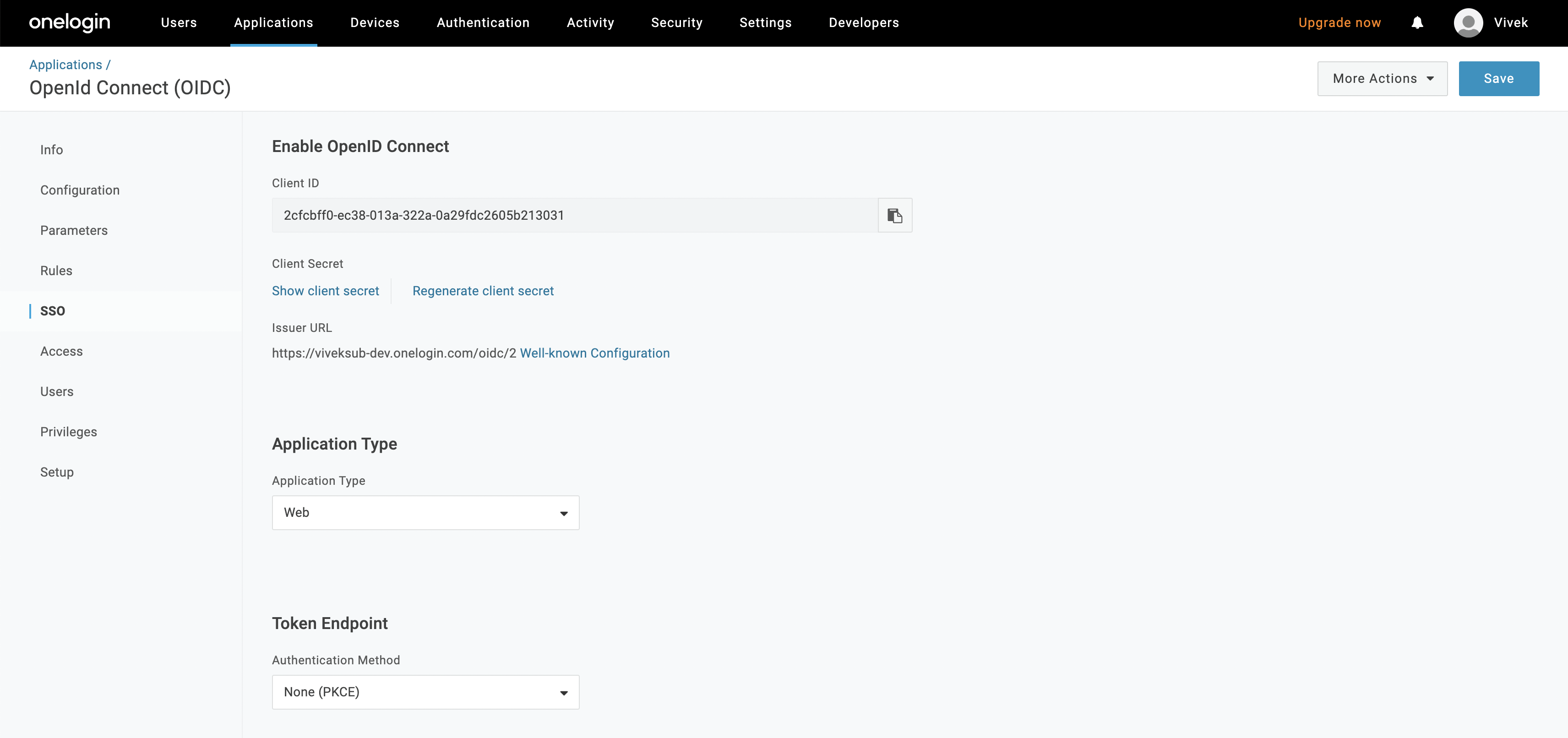
Step 2: Where to find the Credentials
- Go to "SSO" and copy the Client ID
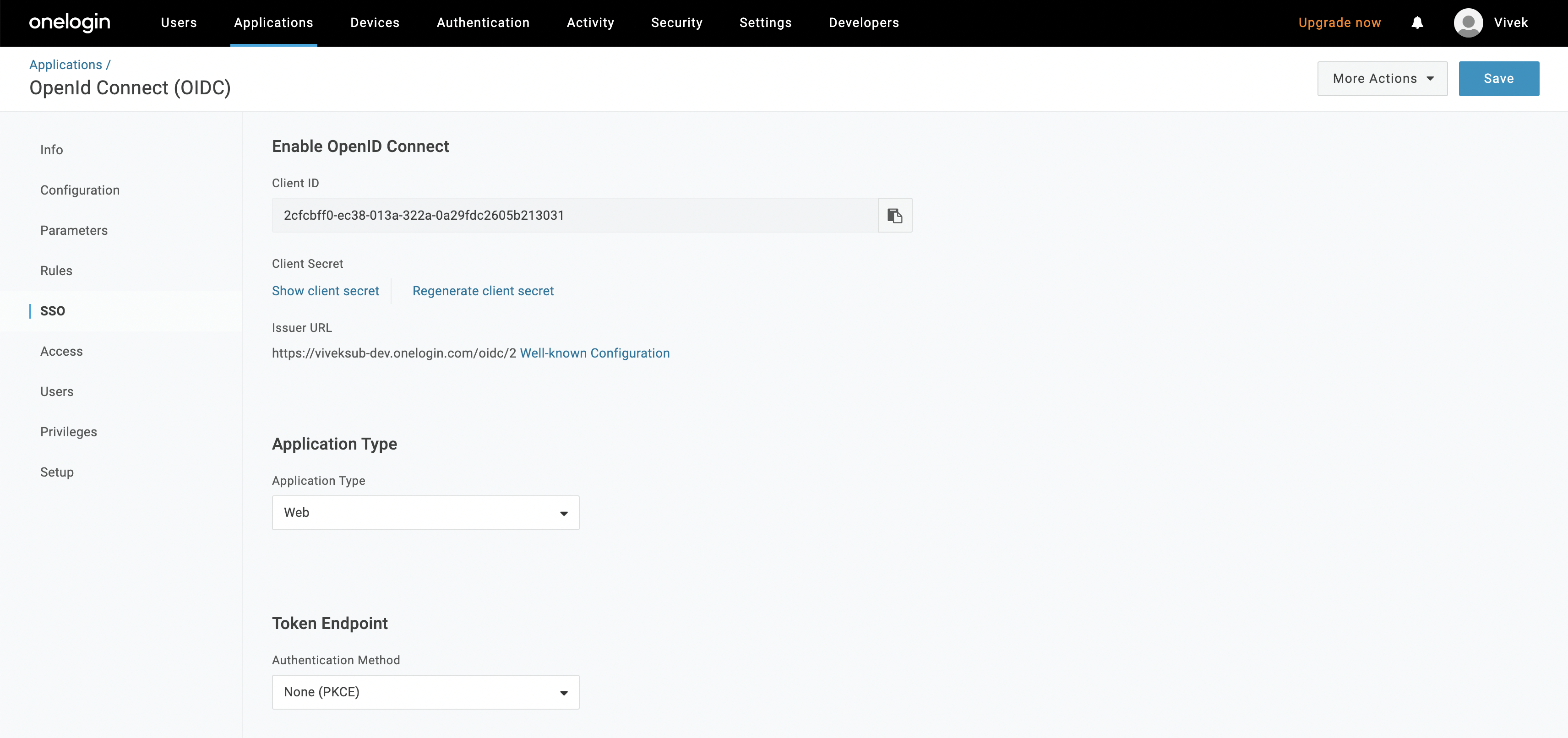
- Copy the Issuer URL
After the applying these steps, you can update the configuration of your deployment:
Configure OneLogin SSO for your Docker Deployment.
Bare Metal SecurityConfigure OneLogin SSO for your Bare Metal Deployment.
Kubernetes SecurityConfigure OneLogin SSO for your Kubernetes Deployment.
Configure Ingestion
Once your server security is set, it's time to review the ingestion configuration. Our bots support JWT tokens to authenticate to the server when sending requests.
Find more information on Enabling JWT Tokens and JWT Troubleshooting to ensure seamless authentication.